In this article we’ll discuss how to clean up a code or script injection that might have occurred on your website that is causing it to try to load malicious content to your visitors, or preventing your site from displaying properly.
Typically code injections are carried out by an attacker uploading a PHP shell script to your account, either by compromising your FTP credentials, or by exploiting usually outdated software that you might have running on your website.
Below are steps for cleaning up a wide spread script injection that occurred on a WordPress site. We could tell that something went wrong because when we tried to view the site today it was simply showing a blank page, and when we went in to investigate it was obvious that a code injection had taken place.
It’s important to note that this would be considered an advanced task and you can only do this with a VPS or dedicated server plan. Additionally we can’t take any responsibility for further damage you do to your website using this clean up method, so if you don’t feel comfortable doing this be sure you make a full backup of your account prior to following these steps or contact our support team for help.
- Login to your server via SSH.
- Navigate to the user’s /public_html directory with the hacked website with the following command:cd ~userna5/public_html/
- Now open up that sites index page, in this case index.php using the vim text editor with the following command:vim index.php
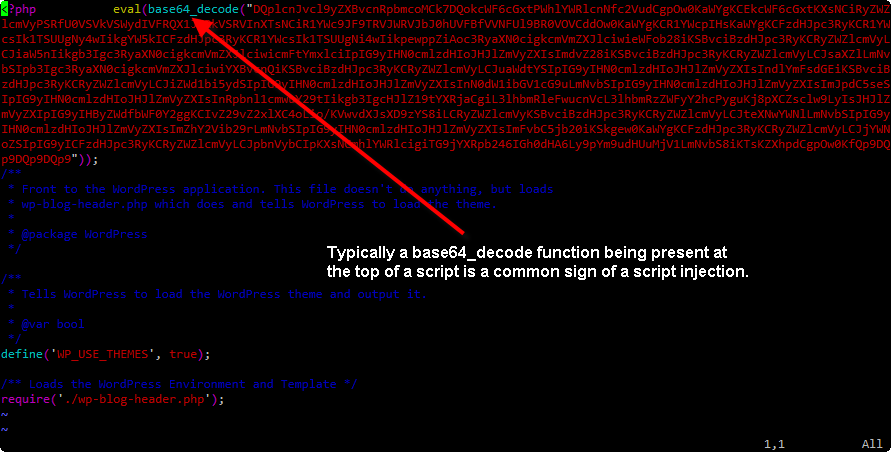
- It should be very obvious at the top of this file that there has been a script injection, usually one of the tell tale signs of a script injection is having a base64_decode function mentioned, especially if it’s at the top of a bunch of scripts.You’ll want to copy the text starting ateval(base64_decode and grabbing about the first 10 or so characters, in most SSH clients simply highlighting text will copy it to the clipboard.
- Now you’ll want to type in the following command using the text that you copied from the /public_htmldirectory:grep ‘eval(base64_decode(“DQplcnJvcl’ ./ -Rl > HACKS
This will take some time to complete as it’s going to look through all of your files for that string, it will be placing them in a file called HACKS.
- Now using that HACKS file in a loop, we want to create a backup copy of each injected script with the suffix -HACKED using the following command in case when we are stripping out the injection it happens to grab any good code accidentally:for hackFile in `cat HACKS`; do cp -frp $hackFile $hackFile”-HACKED”; done
- Now we can use the same loop, but this time using the sed command to replace the code injection of each original file:
for hackFile in `cat HACKS`; do sed -i ‘s#<?php.*eval(base64_decode(“DQplcnJvcl.*));#<?php#’ $hackFile; done
What this sed command is doing is using the -i flag for an in place replacement, the ‘s# part is telling it we’re doing a string replace, with the # symbol being the delimiter of our strings.
The next part is the sting we want to replace, it begins with <?php then we are using .* to state any character at all, followed by eval(base64_decode(“DQplcnJvcl which is the part of the injection we had copied earlier, then finally it ends with another .* to grab all of the rest of the text till finally the last part of the string )); is encountered.
After the second # we put the string we want the first string to be replaced with, in this case just <?php, then we finish up the sed command with another #’ then we put $hackFile after the
full sed command since that will be the file name of the current file in our loop.
Now try to load your site again and hopefully it is back to normal. Depending on the severity of the code injections sometimes this won’t be enough to clean it up, but in most cases this should do the trick.
Originally posted on October 22, 2015 @ 11:15 am
